Beware ransomware: If it’s important, encrypt it
Ransomware has become a menacing and demoralizing factor in today’s computing environment. Ransomware’s rocket-like growth over the past five years has reached epidemic proportions. Every computer user must become more attentive about clicking on unfamiliar links and...
Intel Monday announced three new measures that will be implemented in a future chip designed to bake security into the hardware following last year’s Spectre/Meltdown vulnerability.
Intel Monday announced three new measures that will be implemented in a future chip designed to bake security into the hardware following last year's Spectre/Meltdown vulnerability. Intel Monday …Read more
How can lawyers find cybersecurity solutions that work for them?
As this yearlong series has already covered, lawyers and law firms are sitting on valuable information that could be worth billions to cybercriminals. Additionally, this country loses hundreds of … Read more
Data Breaches Keep Happening. So Why Don’t You Do Something?
Last year was a banner year for the exposure of personal information, and so far this year there has been a steady drumbeat of data breaches, so many that experts worry that people are just throwing up their hands in defeat. Timehop, an app that collects...
Calculating the cost of cyber-risk
Most businesses understand the need to protect networks and data assets if client trust and operational functionality are to be maintained. With the General Data Protection Regulation coming into force on May 25, failure to do so could lead to fines of up...
New PGP Encryption Exploits Are Being Discovered Almost Every Other Day
For more than a week, PGP developers have been rapidly working to patch critical flaws in the legacy encryption protocol used for sending and receiving secure emails; a tool that’s widely relied upon by lawyers, journalists, dissidents, and human rights...
Why 2017 will be the worst year ever for security
Sony. Anthem. The Office of Personnel Management. Target. Yahoo. The past two years have seen one mega-breach after another—and 2017 promises to be the most catastrophic year yet. Security experts have long warned that most organizations don’t even know they’ve been...
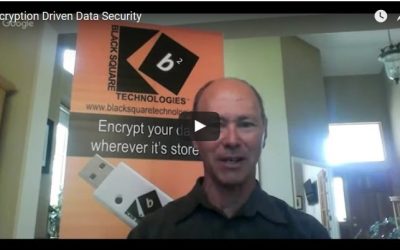
Encryption Driven Data Security Robert Fleming, Founder and President of Blacksquare Technologies participates in Risk Roundup
Austria’s FACC, hit by cyber fraud, fires CEO
The head of Austrian aerospace parts maker FACC has been fired after the company was hit by a cyber fraud that cost it 42 million euros ($47 million). The firm's supervisory board decided at a 14-hour meeting on Tuesday to dismiss CEO Walter Stephan with "immediate...
Ransomware demands are working, fueling an increase in attacks
Emboldened by the wave of successful ransomware attacks in early 2016, more cybercriminals are rushing to take advantage of this lucrative crime spree. Monitoring in the age of devops A combination of cultural transformation and automation is redefining the way...
How Fortune got inside the Sony hack
What Peter Elkind found in his six-month investigation of the cybercrime of the century should terrify corporate America. We have devoted 12,000 words in our July 1 issue to an extraordinary story by Peter Elkind on the now infamous cyberattack against Sony Corp.,...
Millions of hacked LinkedIn IDs advertised ‘for sale’
A hacker is advertising what he says is more than one hundred million LinkedIn logins for sale.The IDs were reportedly sourced from a breach four years ago, which had previously been thought to have included a fraction of that number.At the time, the business-focused...
Survey: 90% of businesses hacked at least once in 2015
For risk managers — indeed for most businesses — among the most disturbing words they can hear are “We’ve been hacked.” What was once something to fear for only large businesses is now an issue for the majority, according to a survey of business risk managers released...
Cybersecurity Breaches Hit Nearly Three in Four Organizations
Nearly three out of four organizations have been plagued by at least one security breach or incident in the past year, with about 60 percent of breaches categorized as serious, according to a new report by CompTIA. The International Trends in Cybersecurity report also...
Cyber insurance can keep your business afloat after a cyberattack
Technology, social media and transactions over the Internet play key roles in how most organizations conduct business and reach out to prospective customers today. Those vehicles also serve as gateways to cyberattacks. Whether launched by run-of-the-mill hackers,...
Black Square Technologies Introduces Hardware Encryption Solution to Solve Data Breaches
Black Square Technologies, founded by Erie resident Bob Fleming, is causing a big buzz in the data and cyber security world. Black Square Technologies has developed its Enigma devices as affordable, real time hardware encryption that work on Windows or Mac OS and...
Building a brand-new Internet
We do not possess the ability to read the future, and yet we can predict with a high level of certainty that we will see more major cybersecurity incidents in 2016 and 2017. The world’s cybersecurity capability is not able to advance in line with the growing...
The two misconceptions dominating the encryption debate
Cybersecurity is a massive challenge affecting everyone –- startups, government, corporate systems and consumers, costing the global economy billions of dollars annually. Tragically, the one solution we are seriously considering — mandating encryption backdoors — will...
Seagate Phish Exposes All Employee W-2’s
Email scam artists last week tricked an employee at data storage giant Seagate Technology into giving away W-2 tax documents on all current and past employees, KrebsOnSecurity has learned. W-2 forms contain employee Social Security numbers, salaries and other personal...
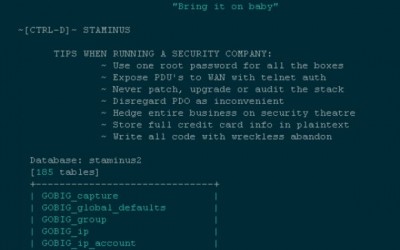
Hackers Target Anti-DDoS Firm Staminus
Staminus Communications Inc., a California-based Internet hosting provider that specializes in protecting customers from massive “distributed denial of service” (DDoS) attacks aimed at knocking sites offline, has itself apparently been massively hacked. Staminus’s...
IRS Reports 700,000 U.S. Taxpayers Hacked And 47 Million ‘Get Transcripts’ Ordered
The IRS has filed an amended statement on the ‘Get Transcript’ hack — which reports that 700,000 U.S. taxpayer accounts were accessed or targeted, and 47 million transcripts have been ordered to date. In January 2014, Get Transcript launched on the IRS website. The...
The Tsunami in 2016 that is NIST (SP) 800-171
2015 was the year of the hacker. There is no segment that was left un-scathed from breaches, attacks, or disruption. Dozens of hospital patient record databases were breached, multiple fortune X corporation’s customer data exposed, and anyone who holds or has held a...
Rob Enderle – Product of the Week
The "Enigma" name comes from an encryption machine Germany developed and used very successfully in the Second World War, until Alan Turing helped crack it. Turing -- who arguably was key to winning the war for the Allies and then, as a twisted thank you, effectively...
First on CNN: Newly discovered hack has U.S. fearing foreign infiltration
Washington (CNN)A major breach at computer network company Juniper Networks has U.S. officials worried that hackers working for a foreign government were able to spy on the encrypted communications of the U.S. government and private companies for the past three years....
Secure your data; you never know who’s looking
By now, it should be abundantly clear that our data is not secure. Over the past 15 years, we’ve seen an exponential increase in organized, methodical cyber-related attacks to steal confidential data, assume identities, drain bank accounts and plunder consumer and...
Did TalkTalk breach the Data Protection Act?
On Wednesday, online criminals decided to attack the UK broadband provider TalkTalk. This wasn’t an attack aimed at interrupting its ability to do business or provide its services, this was an attack the goal of which seemed to be accessing the personal data of its...
Pentagon Farmed Out Its Coding to Russia
By Patrick Malone, Center for Public Integrity The Pentagon was tipped off in 2011 by a longtime Army contractor that Russian computer programmers were helping to write computer software for sensitive U.S. military communications systems, setting in motion a four-year...
Law Firms Face Security Incidents Even as Tech Budgets Increase
When asked in 2015 if their firm was ever infected with virus/spyware/malware, 42.4 percent said yes; 34.9 percent said no; and 22.7 percent did not know. Read more:...
Military clearance OPM data breach ‘absolute calamity’
Anxiety is spreading among defense officials and the military community that the recent theft of federal government data linked to China may affect hundreds of thousands of service members. Compounding those concerns is the limited information made public by the...
Open Letter on the OPM Breach
"It's really frustrating to think that my family might suffer from my information having been stolen." Those are the words of David Thul, who served 22 years with the Minnesota National Guard, was deployed to Kosovo in 2003 and again to Iraq from 2005 to 2007. "My...
Should All Personal Information Be Encrypted?
Last month, the Health Insurance and Medical Privacy Act, or HIPAA, made your electronic medical records a lot safer. As welcome as these changes are, we need to go further. It is time for a federal law requiring encryption of any database that contains personally...
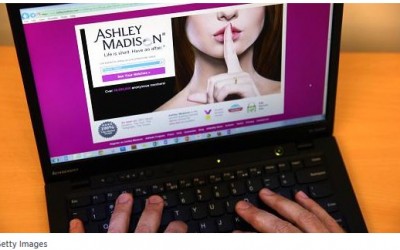
Are Ashley Madison users at risk of blackmail?
The group behind the hack of adultery website Ashley Madison appears to have made good on its threat, leaking the site's user database online—and potentially exposing those users to threats of blackmail. Last month, a group of hackers known as The Impact Team claimed...
Cloud security sector leads cybersecurity mergers and acquisition report
The cyber sector is white hot. According to IDC, the hot areas for growth are security analytics/SIEM, threat intelligence, mobile security, and cloud security. Corporations are investing heavily in these areas to combat cybercrime. The British insurance company...
Lifelock Once Again Failed at Its One Job: Protecting Data
Customers who hired the infamous ID theft-protection firm Lifelock to monitor their identities after their data was stolen in a breach were in for a surprise. It turns out Lifelock failed to properly secure their data. Click here for article
OPM Hack: Can it get any worse?
For those of you that don’t have a security clearance, the information that is on these forms is staggering. Due to the fact that an initial security background has to be complete in order to properly “vet” the individual for access to classified data, applicants are...
Catching Up on the OPM Breach
I heard from many readers last week who were curious why I had not weighed in on the massive (and apparently still unfolding) data breach at the U.S. Office of Personnel Management (OPM). Turns out, the easiest way for a reporter to make sure everything hits the fan...
What does OPM’s data breach mean for you?
A massive cyber breach at the Office of Personnel Management may have exposed the personal and financial information of 4 million employees, putting their credit and finances at risk. But what does it mean for you? It means being vigilant about your credit scores and...
Why the OPM Breach is such a security and privacy debacle
If it’s not already a maxim, it should be: Every big hack discovered will eventually prove to be more serious than first believed. That’s holding to be especially true with the recently disclosed hack of the federal Office of Personnel Management, the government’s...
Federal Union Says OPM Data Breach Hit Every Single Federal Employee
The American Federation of Government Employees claimed Thursday that all federal employees and retirees, as well as one million former federal employees, had their personal information stolen in the federal data breach disclosed by the Office of Personnel...
How to get your CEO ready for a security breach
It’s never been more obvious how great a threat cybercriminals pose to every organization. Hackers, corporate spies, and nation-states have all targeted the defenses of global corporations, and increasingly embarrassing breach reports are making business executives...
Packaging World
Clear package protects, promotes encryption device.
Fines Remain Rare Even As Health Data Breaches Multiply
In a string of meetings and press releases, the federal government’s health watchdogs have delivered a stern message: They are cracking down on insurers, hospitals and doctors offices that don’t adequately protect the security and privacy of medical records. “We’ve...
You’ve been hacked. Now what?
What should a company do after it’s been hacked? It’s a question Target, Home Depot, Sony Pictures Entertainment and others have had to ask over the past year or so. And it’s likely that other organizations will be facing the same question over the coming months....
Top 10 Myths About Identity Theft
Each new data breach and phishing scam alert is accompanied by a wave of cyber security articles and commentary. The tone of these stories can range from panicked to apathetic. But the facts can't be ignored: identity theft is an epidemic in the United States....
People Want Safe Communications, Not Usable Cryptography
For encryption to be widely used, it must be built into attractive, easy-to-use apps like those people already rely on. Security and privacy expert Micah Lee recently described how he helped set up cryptographically protected communications between whistleblower...
Moda Health looks to ease members minds on medical data theft
In lieu of the proliferation of data breaches across all sectors, but particularly in healthcare, a Portland-based health insurer is offering what it says is deeper protection against medical ID fraud for members with the launch of its MIDAS alerts with ID Experts....
You’ve already been hacked
There are two things now driving the security industry: 1. The bad guys are already inside. 2. New platforms — cloud and mobile — have arrived. …Both are forcing a different set of technologies, and the creation of new kinds of companies. If we take the new...
FBI Director: Every US Company a Victim of Hacking by China
James Comey, director of the US Federal Bureau of Investigation (FBI), has said that state-backed hackers in China might have hacked every big US company, stealing corporate secrets worth billions of dollars. Speaking on CBS's 60 Minutes programme, Comey said China...
Box gets customer-managed key encryption
Fresh off its initial public offering, cloud file synch share and storage company Box has a new Enterprise Key Management (EKM) offering out this week that analysts say could ease customer concerns with using a cloud-based service. Box’s EKM uses Amazon Web Services’...
Lessons from Anthem
The breach involving 80 million records at the nation’s second-largest health insurer fulfilled the warnings many have offered for years: there is no such thing as a secure electronic health information system. Large numbers have a tendency to concentrate the minds of...
Kaspersky Says NSA Planted Stuxnet-Type Cyberweapon In Hard Drives To Spy On Computers Worldwide
Security research firm Kaspersky Labs says it has uncovered what is likely the greatest threat in the history of computer security and that the group's sophistication level, including the ability to infect computer firmware and the use of multiple malware systems, is...
Kaspersky Lab reveals spyware on the world’s most popular hard drives, suspects the NSA
The conclusion that has been reached is that your passwords stored on your computer’s hard drives are now totally vulnerable and visible by this spyware.Therefore, you should store passwords in a device like Enigma, where the passwords cannot be seen or hacked. Click...
Did President Obama’s Cybersecurity Proposals Go Far Enough?
Did Obama's Cybersecurity Proposals Go Far Enough? 1/21/2015 9:23AM Did President Obama's cybersecurity comments and proposals in his State of the Union address go far enough? PKWARE President and CEO Miller Newton takes a look. Click for video